This one has been a long time coming! To be honest networking is not my strength. It’s one of those areas where I wish I’d been a network admin to work out some of the practicalities of different network models, but here goes anyway!

DNS
DNS is short for Domain Name System. Essentially it’s the same principle as the address book in your mobile phone. Rather than you having to remember all the phone numbers of the people you know, you can just look up their name, tap a button and you are instantly phoning them. You may be one of the people that take pride in memorising peoples phone numbers (if they still exist), but imagine for a moment that your address book contains millions of names, that would be pretty much impossible.
The DNS system does the same for the internet, it takes the domain name you enter, or click on in a search, and converts that to a server address that the network and routers that are tasked to get you to the site will actually understand.
To give you an example of this, we all know google.com, but would you remember it’s IP is 142.250.217.110 (when I checked anyway, but yours may be different – use https://www.site24x7.com/find-ip-address-of-web-site.html to find out). You can enter that IP directly in your web browser and you will end up at Google. It’s a lot easier remembering google.com though.
So what has this got to do with security? Well you can imagine that if a malicious person was substitute their own entries into DNS, they could send you anywhere they wanted rather than to the site you were expecting. For example you could change google.com to point to 40.89.244.232, which is duckduckgo.com. Arguably this would be a better choice, but it’s not where you wanted to go. Now imagine if you could create a fake bank site and send someone to login to that rather than their actual bank. All of a sudden the person being attacked has just handed over their bank username and password to the attacker!
DNS can also be a great security measure to stop phishing attacks. There will be more of this later, but imagine a smart DNS system that could check a link you just clicked and say “STOP, that site is potentially malicious”. Even more than that, online advertising can be a source of malware too. DNS can block that for you.
Recommendations for DNS
The great thing about DNS is that you can set where these addresses are looked up on your router, so you can protect your network and users just by moving from default DNS settings that probably your ISP controls to something a bit more secure. There are loads of options you can consider, and I won’t be able to go into all of them here. I would encourage you to do some digging around for yourself though.
DNS servers that deserve special mention though include: –
Open DNS – These are one of the first providers I became aware of and used for some time. Their Prosumer small business account on https://www.opendns.com/home-internet-security/. You can see that they offer many of the features mentioned above.
Pi-hole (https://pi-hole.net/) – A role your own solution which requires you to have a small raspberry pi based system on your network. This gives you amazing control of your DNS and your network in general, for the amazingly low price of free, plus the cost of the raspberry pi and the cost to power the device.
Synology NAS DNS Server – I must admit that I’m a bit of a Synology fanboy! They provide some great hardware and software combinations that are hard to beat. I haven’t played with the DNS server system available on their NAS, but it would be a good combination if you are already running their system for storage (more later).
NextDNS (https://nextdns.io/) – For me, NextDNS hits the mark! It has all the features we mentioned above and a few more besides. It’s easy to protect your mobile devices when you are out on the go using their straightforward app, their privacy policies seems to be solid and it’s really cost effective (https://nextdns.io/pricing). For me, I can get away with the Pro account that costs just US$30 per year! That’s a real bargain for what it offers.
As you can probably tell, I am an NextDNS user, so the next section will go through the settings I use for my account: –
NextDNS Features
First things first. If you chose to use an online DNS system, you need it to be fast! There’s no point in picking a secure system, if each DNS query (and there are a lot of them) is so slow, your whole network slows as a result. If you go to the bottom of the NextDNS homepage at https://nextdns.io/, you will see a map and an indication of the response time for a DNS query. Make sure your on a reasonable network and check to see there’s a server near you and that the response time is quick.
Once you have created an account, there’s an array of settings, some of which are on by default and others not. Settings to note, and that’s essentially all of them, include: –
- Use threat intelligence feeds – these are lists of known malware that are updated in real time. You need this one on.
- AI driven threat detection – although I’m not sure how this could work, I have it switched on anyway!
- Google Sage Browsing – Google looks at millions of websites per day and identifies any that are unsafe. Switching this on will use Googles list and block access to these sites and will not allow bypassing of this block (which you can do in the browser).
- Cryptojacking protection – Enabling this will stop your device being used to mine (generate) cryptocurrency.
- DNS Rebinding Protection – this stops your device from obtaining data from other devices on your network. There’s a great description of DNS Rebinding at https://www.paloaltonetworks.com/cyberpedia/what-is-dns-rebinding, but it’s safe to say, you want it on.
- IDN Homograph Attacks Protection – This uses similar but different letters to the genuine domains to make it look like you are logging onto an known website, when really you are logging in elsewhere.
- Typosquatting Protection – This is similar to the above, but is based on common misspellings like fcaebook.com instead of facebook.com.
- Domain Generation Algorithms Protection – Blocks domains generated often by malware so that the malware can “phone home” for control information.
- Block Newly Registered Domains – This one of not on as standard, however I have it switched on. It blocks domains that have been registered less than 30 days ago. This can be a problem if you are say in the business of generating websites, but my experience is genuinely positive in that I don’t see many false positives. Newly registered domains are often used in phishing attacks etc.
- Block Child Sexual Abuse Material – turn this on!
Heading into the privacy settings there are also some useful things to switch on. In my system I have NextDNS blocklists switched on which is the default, but click on the “Add a blocklist” button and you can also add other lists too from a huge range they have available.
I have not got native tracking protection turned on, but you can block tracking for Windows, iOS, Amazon Alexa, Samsung etc. I have an iPhone and I know the standard lists already blocks a lot. You have to give them something for their ‘free’ software I guess!
Blocking third party trackers disguising themselves as first-party is a good idea, but can give you some odd results if you are a web developer like me. I have it switched on though.
Lastly on this page is the setting to Allow Affiliate & Tracking links. You often see these for product reviews etc and I would guess that NextDNS strips off the tracking component, usually added after the ? in the url. This one is a difficult one! If you look at a lot of reviews before buying, it might be a good things to switch on and allow these, as it means the person writing the review will at least get paid for their work. Be careful though with this setting as unlike the others you switch it on to allow the links.
Parental Control Settings
You may think that parental control settings are not applicable to small business, but there are some useful settings in here that are not available elsewhere and can be used to improve your security. Before I go further though a lot will depend on what you have on your network and how you set up Next DNS.
If you set up NextDNS on your router, it will affect ALL devices on the network and any guest networks you set up. So if you have personal devices that may want to access content that you don’t want on work devices, you have probably to use NextDNS on a per device level, which is a shame as you lose it’s security and tracking benefits on other devices. So if you feel the need to use the type of security where sites and access are limited, you have to think carefully about your network segmentation.
So what are the main features of the parental control section? You can block specific or broad categories of apps and sites. Why is this a good idea? It’s not about your staff wasting time when they are supposed to be at work, it’s more about securing yourself from data exfiltration IMHO. Blocking access to things like Signal, Telegram, Messenger etc., may stop an attacker that manages to get into your network, or staff sending out data so that they can access things later on.
The other great setting in Parental controls is the ability to Block Bypass Methods. Essentially that tries to stop people trying to bypass all the controls you have set up in NextDNS. If you have a child at school, I’m sure you’ve heard of all the ways they try to get around schools sometimes overly restrictive filtering policies.
Deny and Allow Lists
These are self explanatory. However you may find that you need to add sites to the Allowlist that you might not necessarily want on there if sites don’t work as expected. For me for example, I had to add a bunch of Google domains so that I could access and use Google Analytics.
Analytics
This is the frightening bit! It gives an overview of exactly what is happening with your web requests. It also gives you the information you need to tweak your settings so the NextDNS works for you. The following is an overview of just one device on my network for the last 7 days: –
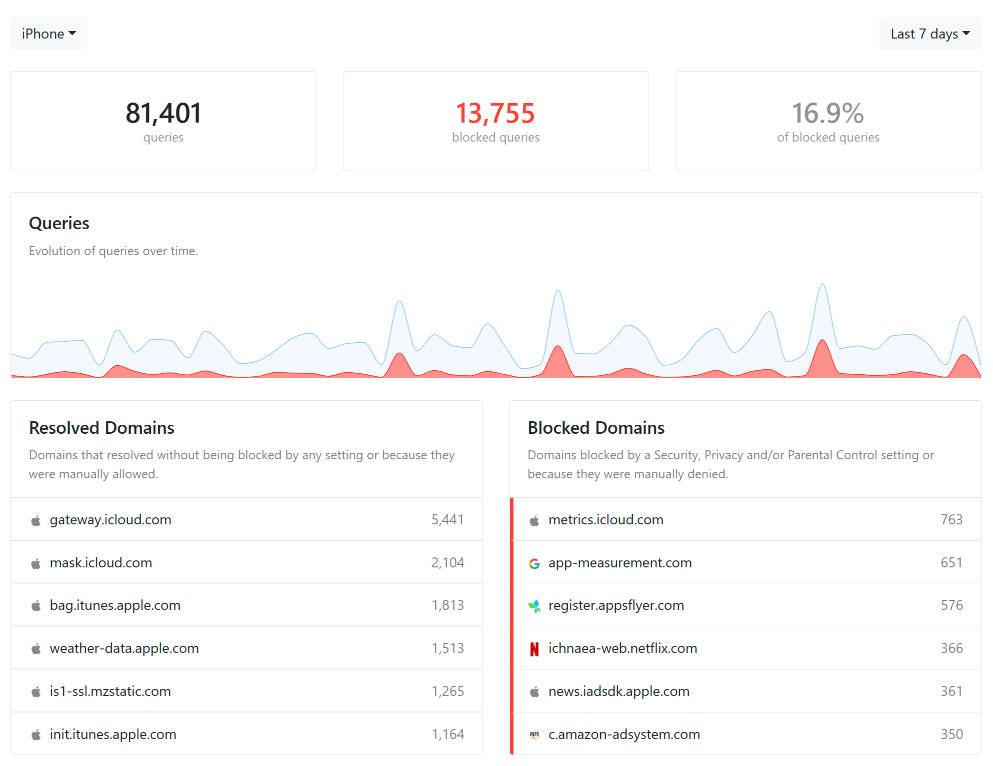
As you can see, there’s a lot of domains that are queried by Apple on an iPhone. On the blocked side on the right hand, NextDNS is blocking some icloud metrics, a bunch of what I assume to be in-app analytics tracking and a company called appsflyer which I must admit I hadn’t heard of, but also seems to be in-app analytics.
If you are experiencing problems in apps, this is a good place to look as you may need to add some of these to your allow list.
The other section in here that I find good to review is the map at the bottom of the page. This shows which countries internet traffic goes to. You can mouse over different countries to see what is going there.
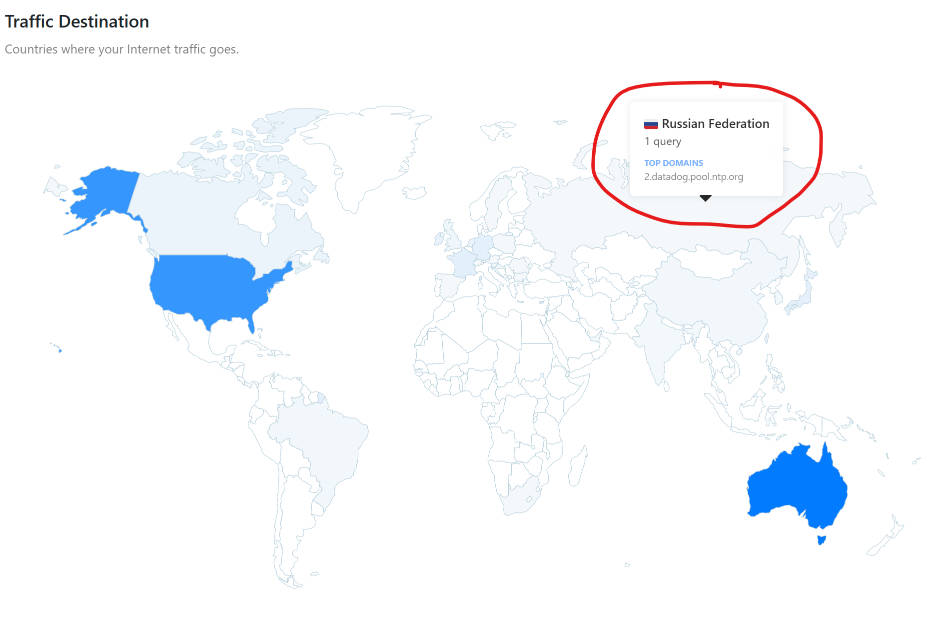
Here you can see that at some stage this iPhone accessed an unexpected domain in Russia. This was actually a time server, so nothing to be concerned about, but you can imagine that if you see a large amount of traffic going to an unexpected country, you can block it in the Deny List.
Settings
I’m going to skip over logging at the moment as really you need to change some settings first. For a business I believe that it’s important to log, but not to use those logs for anything other than security. If you think you have a staff member that’s on social media all the time when they should be working. Talk to the staff member and maybe block social media in the parental settings, don’t look for evidence of what they have been doing in the logs. If you use logs wisely they will not be seen as infringing privacy, they will be seen as the security measure that they should be.
In settings I therefore have logging enabled and log both the clients IP and the domains. That way if a system does get hacked, you can trace that back. The retention period you set really depends on you. Mine is set to 3 months, but considering that a network intrusion may mean someone has been on your system a significant amount of time (sometimes over a year), you may want to extend that. My rule-of-thumb theory for 3 months is that its a long time for a relatively small business holding no state secrets!
I chose to hold data in the EU, just because their privacy controls are the strongest.
Other settings that are useful are setting up a block page. That shows the users what has happened if they just get a blank page (and it has happened).
One that I’m not sure about is Rewrites. This is a useful feature for many businesses when they can use NextDNS to route traffic to say internal subdomains. For example, if I had an intranet (which I don’t) and used an external service to provide that which had a url of say https://simonsintranet-wghdfwh.xyz123.com you may want to rewrite that to say https://intranet.webxopt.com. Much easier to remember for your users. However this comes with a down side. If someone breaks into your NextDNS account, they can redirect anything to anywhere! Make sure you add your 2 factor authentication to minimise the chances of this happening! I’d love to see NextDNS limiting this to say higher level accounts, or even creating a ‘super-admin’ that gives access to this feature but leaves it off the normal interface.
Lastly, assuming that you have set up your account correctly in settings you will see all DNS queries going through the system…and there will be a lot of them! You can search by device, use the search box to find particular urls, limit the results to blocked queries etc. I’d like to see a date range search in here too, but I guess as it’s only used occassionally, a bit of scrolling is ok.
How to Use NextDNS
The things I like most about NextDNS is that you can cover both your network and the devices that are used outside your network. My recommendation would be to add NextDNS to your router settings. That way all DNS goes through them, but you can just install on a per device basis. NextDNS provides instructions, but setting up on a router can be tricky! Don’t forget though to add their app you all devices that may go outside the network. That way they are still protected.
Does it Work?
The short answer is YES!
I have had 3 cases where people on the network had been tricked into clicking a link they shouldn’t have. In all cases NextDNS blocked the queries and they didn’t end up on the phishing sites they clicked on.
Next Article
The next article, we will take what we know from our router and look at segmenting your network. This is a really important step in keeping your work devices separate from everything else.