It has been a long road to this article! Knowing where and how to start, when this was the area I skipped over the most in my reasearch paper at Griffith Uni., has been a difficult thing to do. However, I finally realised that we should start at the start, and that’s the first and probable the most important piece of networking equipment, your router.
Routers
The router is likely the first piece of networking equipment we have as a small business. It is either separate from a modem, or you may even have a modem that connects into your router.
So what does a router do? Essentially, it’s all in the name! A router sends web traffic to or from a computer on your network. It’s what knows that when you request a web page in your browser, that it should send that to your computer and not to someone else’s. Routers however do many more things than that and are an vital part of your network security and performance. They block traffic that hasn’t been requested, stopping attacks and can segment your network for improved security (more later).
Routers also control our WiFi, which, if you are like me, is the way I handle my networking, as it’s just easier to do than running cables and is usually ‘fast enough’ that personally, I don’t need the hassle of running a super quick cabled connection. However, we will look at cabled networks later too.
The first thing to consider is the router you should use. When I joined my Internet Service Provider (ISP), they helpfully supplied a free router. My first rule of routers is that you should instantly put this to one side and go and buy something a bit better yourself. Why would you need to do this? Firstly because it is unlikely to be powerful enough to handle small business traffic and secondly, because it will not have many of the security features you require (and is often configured to allow your ISP into your network, which is a recipe for disaster).
Buying a Router for Business
I mentioned above that an ISP supplied router probably isn’t powerful enough for small business, so what exactly do I mean by that? The graph below shows the problem.
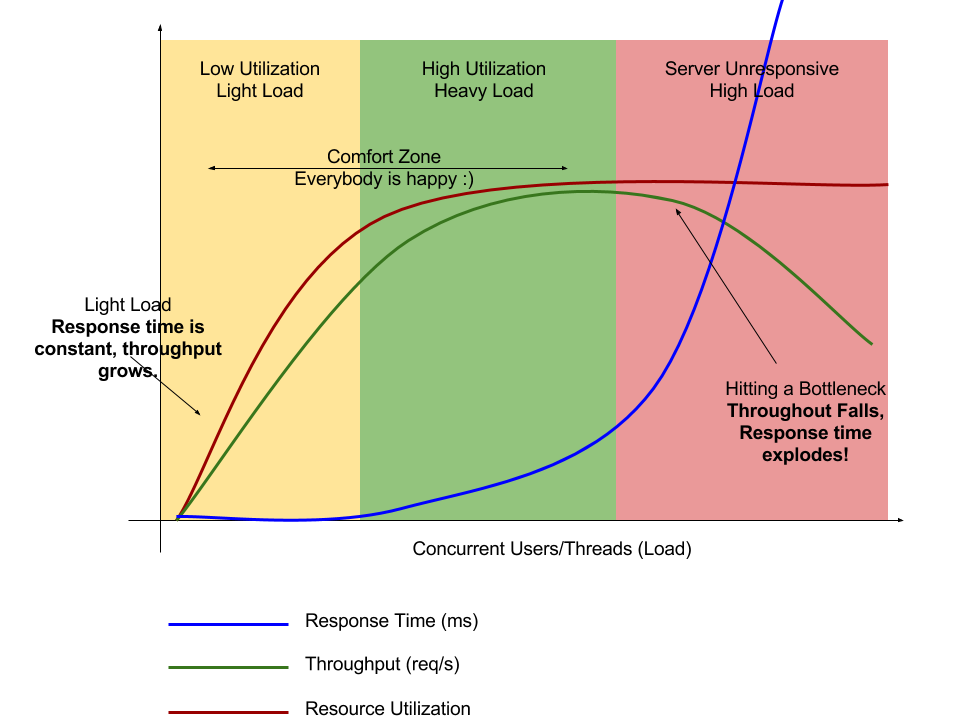
This looks a bit scary, but actually it’s quite simple. As more connections to the router are made, from either multiple or single machines, you move from the “Comfort Zone” into the “unresponsive” zone. This essentially means once you get past a certain point, no matter what the manufacturer or ISP claims, the response time will start getting worse and worse, your network will get slower and your work will become limited by the speed of your network.
So, not all routers are equal in other words. A cheap, low powered router typically supplied by an ISP might even offer WiFi 6e (latest at the time of writing) but will have a low end processor, that will run out of capacity quickly and likely put you in the “unresponsive” zone. They will still likely be outperformed by an older router with a higher end processor in a small business situation.
Routers I would recommend for small business, can still be bought at your local electrical store or Amazon, but may cost you a few hundred dollars, but they are worth it…really! A few hundred dollars down will make your life as a small business so much easier! I would recommend routers such as: –
- Synology RT6600ax – a great small business router with strong security features (the router I personally want)
- Ubiquiti routers – Amplifi
- ASUS RT-AX routers or similar
- Netgear Nighthawk
- Palo Alto Networks – Okyo Garde (I just like this one because of the security features, but have no experience with it)
Personally I have an ASUS router that I have found to be super fast and has a lot of the features I need built into their software. Yes I want the Synology RT6600ax and may consider an upgrade in the near future for it’s stronger security and network segmentation features (more later).
Router Configuration
I am not going to go through general router configuration, as they are usually pretty straight forward these days. However, getting back to security, there are a few rules you should follow: –
- Disable uPNP – this is a feature filled with security flaws that should never be enabled, or even allowed space on routers!

- Disable access from outside your network. However convenient it may seem, accessing your router configuration from outside your network is asking for trouble. Just disable it and sleep better at night!

- Change your routers default password. This one goes without saying.
- Activate auto update. Yes, the better routers update their software, and surprisingly often. Many routers allow you to set this to happen automatically at night so you don’t need to check for updates yourself.

- On a busy network, I would also set the router to automatically reboot every night to clear caches, find the optimum channels to operate in etc.
I would also encourage you to have a look around your router settings. On my ASUS I have enabled some antivirus checking (although could be a potential privacy concern) using AiProtection which is a service from Trend Micro and is free on the ASUS router I use. This isn’t blocking a lot if I’m honest, but it has blocked about 300 requests in nearly 3 years of operation. This isn’t my only protection that blocks malicious urls, but it is worth switching on anyway. I did mention above that there was a potential privacy problem. Essentially it isn’t clear what information Trend Micro gets and how they use it. If your work involves some sensitive sites or downloads, it might be better to switch this off and mitigate the risk of malware or scam risks using network segmentation.
Another useful router feature for security is to also enabled logs so that I can see traffic to individual systems. From a security point of view, this means you can potentially see changes in traffic that might mean data is being extracted from your system.
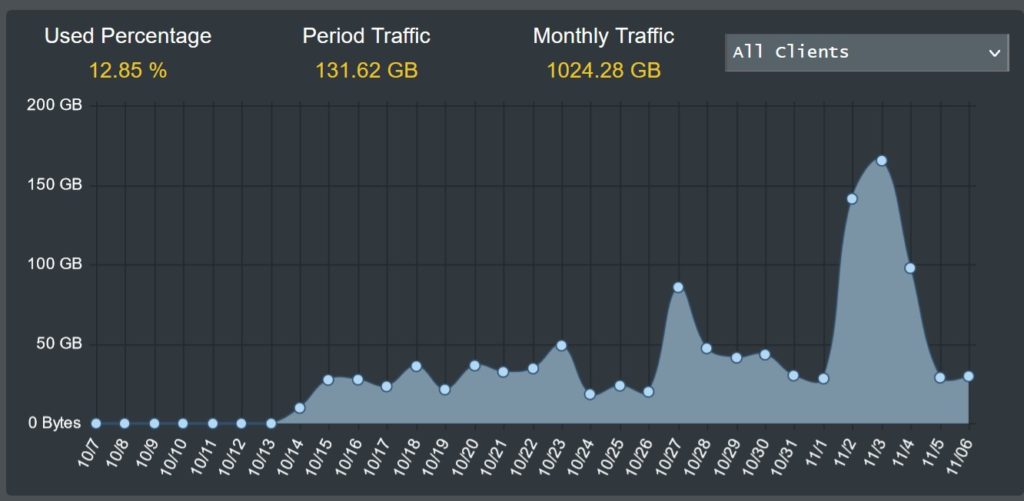
As you can see from the above, there was a large peak in traffic from 2/11 to 4/11. Looking at the client list shows that this relates to a new PC, which was updating and downloading some content. Looking more closely at that PC, I can see some of the bloatware that was removed after installation, and some that I now know I should remove (Clash of Clans).
At a later date you can see that there is an unknown client on the network that downloaded a significant amount at 19-20h. As it happens I know what this was, but this is the type of information that is useful to be able to see. Also it’s very important to keep an eye on uploads which may indicate that data is being taken out of your network.
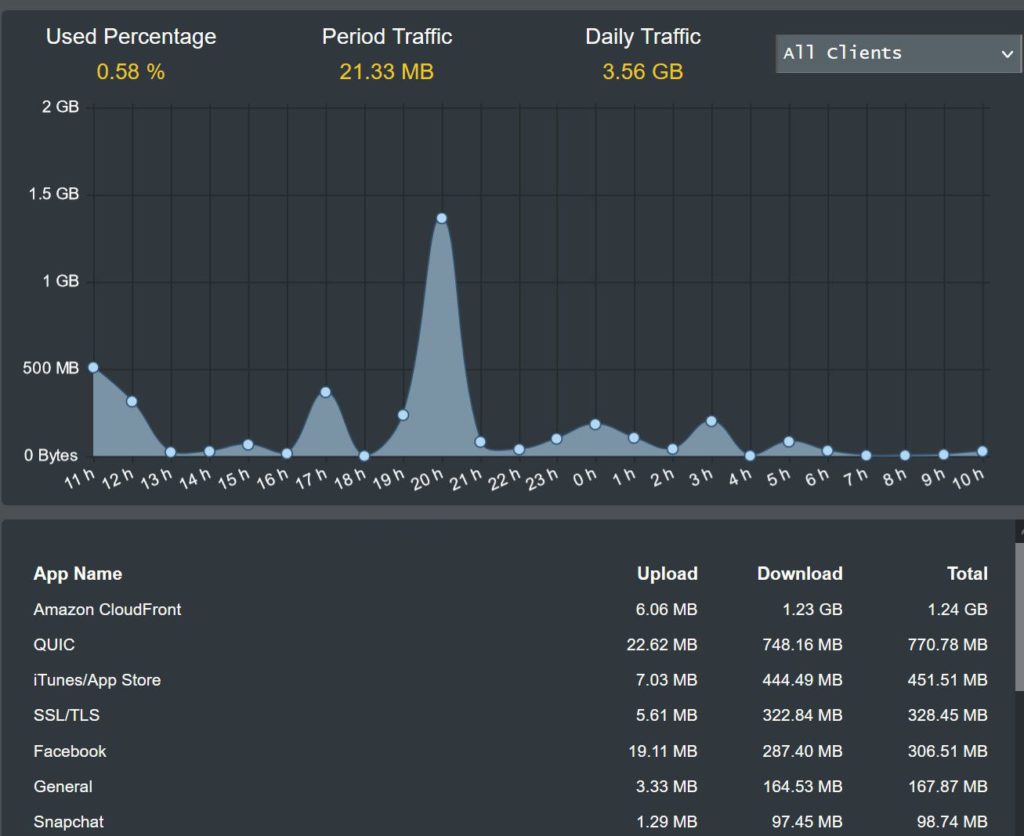
Using Your Router for Security
Apart from network logging, which as you can see for the above, is very useful, there are also other great features of most routers you can use for security. My favourite of these is looking at device lists and from those identifying devices where you segmenting your network.
The most obvious example of network segmentation is the ability to create “Guest Networks”. The Guest network is a great thing! You can totally isolate devices on the guest network from your business devices on another network. This leaves things you can’t control isolated from things you can. I’ll give a couple of examples of guest networks for you to set up.
IoT (Internet of Things) Network
If you are like me you probably have voice assistants, health monitoring devices, TVs, cameras etc that all need an internet connection. Many of these probably have old software that can’t or won’t be updated by the manufacturer. These are an attackers paradise!
Getting into your network via a security camera, may not seem likely, but it’s a typical way in for many attackers. Probably the most famous IoT attack was a Las Vegas casino which got hacked via a WiFi fish feeding device on their network.
We can learn from their mistake and make sure that all our IOT devices are isolated away from our business operations by setting them to all connect to an isolated guest network with access only to the internet.
Visitors Network
If your business or even your home often has visitors that need or want access to the internet, a visitors network is a great way to isolate their ‘uncontrolled’ devices from your business network.
If you have kids like me, you’ll know this problem well, when a friend of theirs comes over and wants to get on the internet as their mobile plan is running low, or they want to do their homework. They are more than likely using devices that are not well maintained or updated, may have ‘free’ versions of paid for software (which often come with extras you really don’t want), and at the very least, you do not know whether their device is a security concern or not.
This is an ideal case for a guest network. Why take the risk of potentially giving them access to your business machines if you don’t need it? Set up a guess network and just give them access to the internet connection they want.
Device List (Network Map)
This may seem like an interesting, but relatively useless section of your router software, but it is really the key to many areas of security and the network segmentation we mentioned above and protecting your business by segmenting your network into business groups (and non-business groups).
What does a network map do? It lists all the devices connected to your network. This will be your key to a lot of other network security we look at into the future, so it’s worth taking the time to look at it closely.
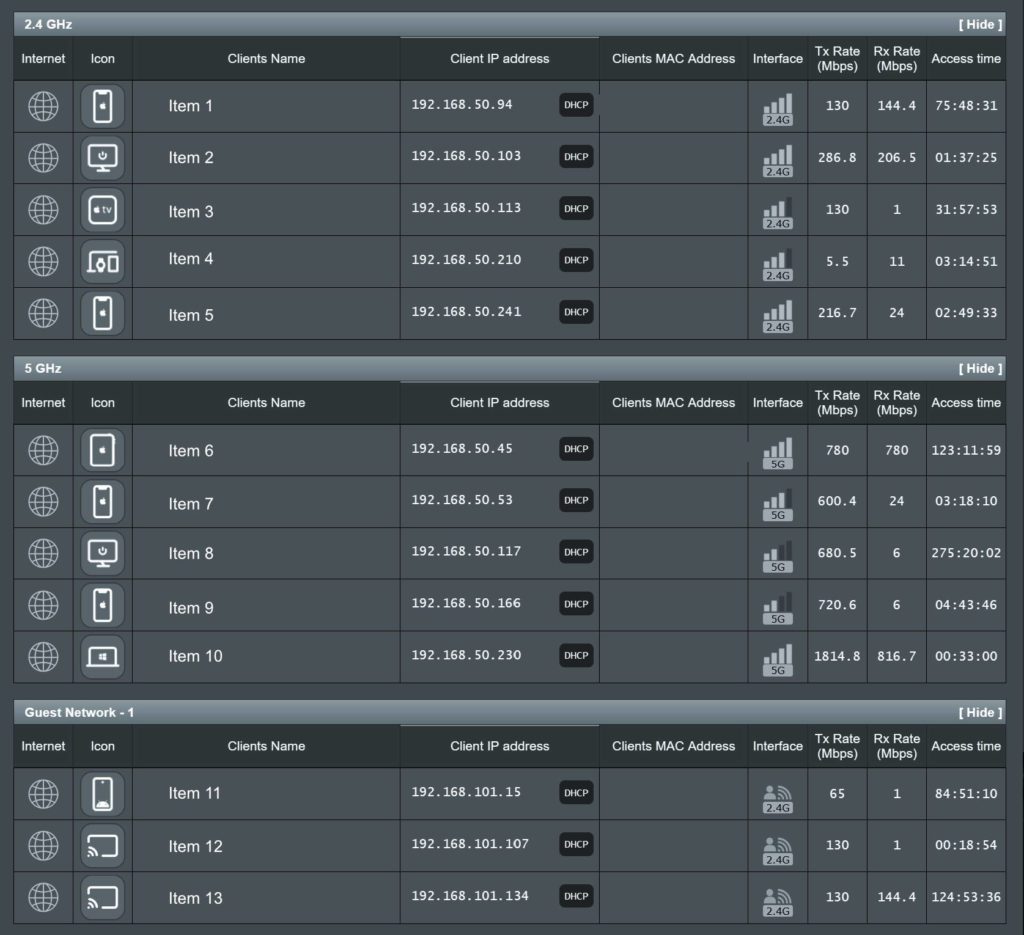
You can see my network here with 13 devices connected at the time. I have blanked out the names and MAC addresses for my safety, but the icons might give something away! You can see too that my router has divided the devices nicely into the 2.4GHz. 5GHz and a Guest Network.
What you will see in the clients names area is either the name of a device you recognise (eg your phones name) or a series of letters and numbers. The first thing you need to do is to be able to identify every item on this list. Those odd jumbles of letters and number are a computers way of identifying an individual item. This is what’s known as the MAC address, but as is, it’s pretty useless to you, so you need to translate that into something that you, as a person, can easily identify, like “Steves Laptop”. There are a couple of ways to do this. The first is to go through devices you know are on the network, but you can’t identify from the list and look for their MAC address in their settings. For example you can check MAC address: –
- On a PC in Settings, System, Network & Internet, click on the network you are connected to (WiFi or ethernet/wired), select your network, in the Properties section you will see Physical address (MAC)
- On an iPhone the MAC address is known as your WiFi address. To find it go to Settings, General, About and you should see the WiFi address.
Obviously this way has some issues as it can be quite time intensive for a larger number of devices. Personally, the approach I like to take is a bit more draconian! I warn everyone that I am about to cut off devices on the network where I do not know what they are, then I use the router controls to cut them off. Weirdly on my ASUS router, that is really easy to do on their mobile app, but I have yet to find similar controls on the desktop. As people jump up and down wanting their access back, you can go through the device list on your mobile, switching things on and off so that when they do get access, you know what you have just switched back on again. Take this time to adjust your router with a name for the device that you will recognise. This is again easy to do. In the case of my ASUS router, via their app.
In reality a hybrid approach to identifying devices connected to your network is probably best. Identify those you know are there using the MAC address method and those that you aren’t sure of by switching off their access. What I have found is that once you have done this once, keeping an eye on your network via a mobile app and just switching off access to anything new you don’t recognise is a good practical approach.
Exporting Device List
Another useful feature often found in a routers device list is an export feature. Make sure you do this and you should get a list that you can open up in Excel of the devices on your network. Please do this as it will be the starter for the next article on network segmentation.
Note that you might need to check this list a number of times as things go on and off your network on some routers. Others may keep a list of all devices that connect.
Summary
This has been a quick look through routers and their security options. As a summary: –
- Don’t use an ISP supplied router. Buy something more powerful.
- Disable uPNP and access from outside your network
- Change the default password
- Enable auto updates if this feature is available
- Use router based security unless there is a privacy reason not to
- Enable traffic logging to see unusual patterns
- Move your IoT devices and any home devices to separate guest networks
- Run through your devices list to identify all devices on your network
- Export the devices list for use in the next steps
The next article we will start to use the device list downloaded from your router to think about segmenting your network and keeps tabs on these devices to make sure they are not a security risk. We may also consider some additional router level security to protect all devices from malicious websites and links.